GitHub’s advisory database enables repository maintainers to identify, manage, and address vulnerabilities in their projects. These advisories allow developers to track vulnerabilities through a centralized dashboard, notify affected users, and provide guidance on resolving security issues. Security advisories are tied to GitHub's vulnerability alerts, which notify repository owners and contributors about dependencies that may be at risk.
Key benefits:
- Centralized tracking: Manage vulnerabilities in a dedicated space.
- Automated notifications: Ensure developers are aware of security risks.
- Collaboration tools: Collaborate with security experts to resolve issues.
Receiving GitHub advisory notifications
GitHub advisory notifications are sent to project owners and team members whenever a new vulnerability is detected. These notifications include details about the affected package, its severity, and recommendations for mitigation. For example, if your project uses a version of a library with a known SQL injection vulnerability, GitHub will notify you via email and display the issue in the "Dependabot alerts" section of your repository.
Managing GitHub advisories
To effectively handle GitHub security advisories, follow these steps:
- Enable vulnerability alerts Ensure your repository has vulnerability alerts enabled:
- Go to the repository settings.
- Navigate to "Security & analysis".
- Enable "Dependabot alerts".
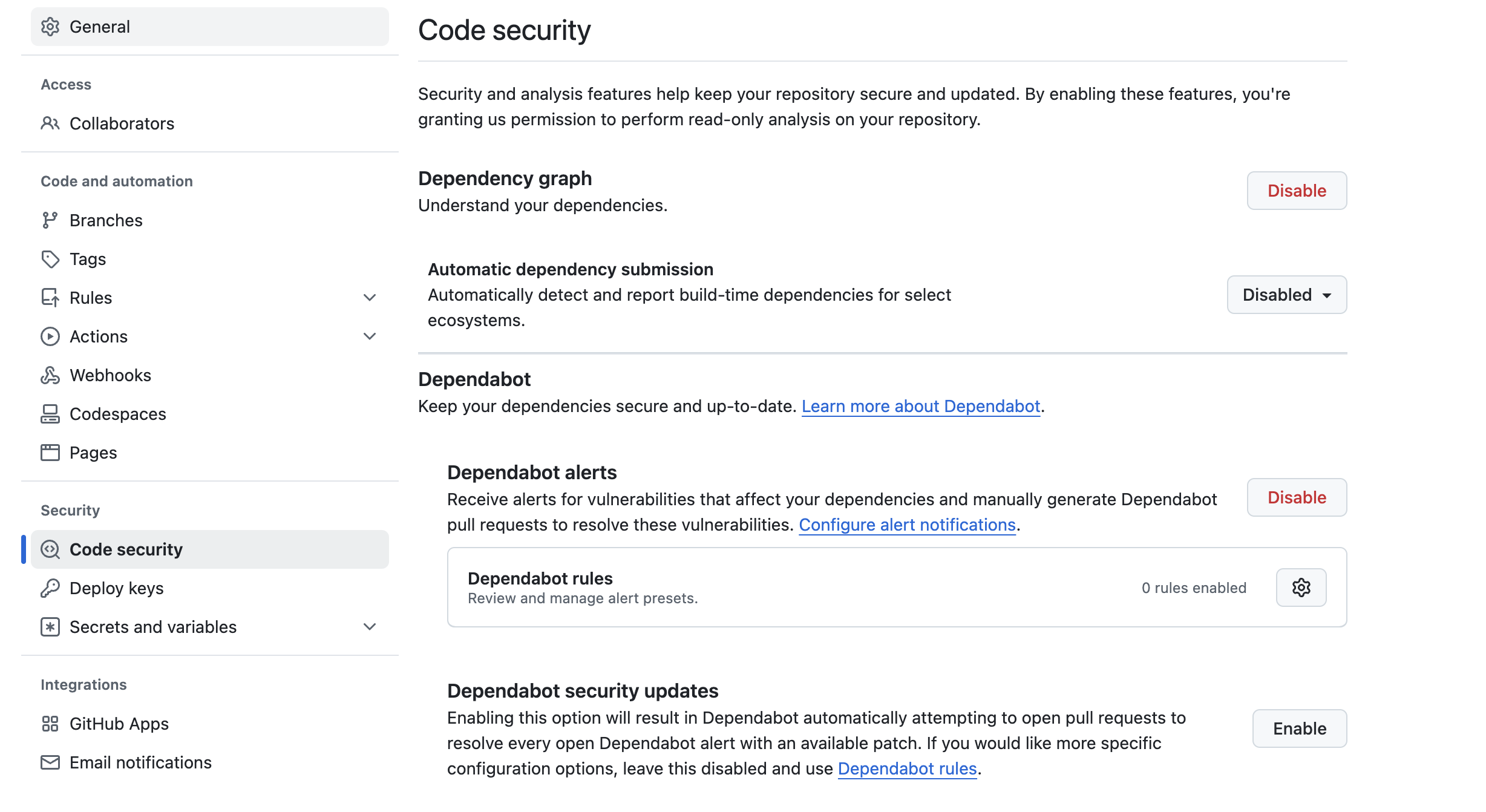
Review vulnerability details In the "Security" tab, examine the advisory details:
- Affected versions.
- Severity levels (low, medium, high).
- Links to CVE (Common Vulnerabilities and Exposures) databases.
Create a security fix Collaborate with your team to address the vulnerability:
- Open a branch for the fix.
- Submit a pull request with the resolved dependency or patch.
Leverage Graphite Protections Use Graphite Protections to enforce security policies:
- Require specific reviewers for security-related changes.
- Define CI pipelines that validate security patches before merging.
- Override standard merge rules for urgent fixes, such as applying the "oncall-override" label for critical issues.
GitHub vulnerability alerts in action
Vulnerability alerts are automatic when you use GitHub’s dependency graph. This tool scans your project dependencies and cross-references them with known vulnerabilities.
example workflow:
- Dependency scan: Your project includes
library-X@1.2.0. - Advisory match: GitHub finds
library-X@1.2.0vulnerable due to CVE-2023-4567. - Notification: Team members receive an alert with recommendations to upgrade to
1.3.0. - Resolution: A pull request is opened with the updated dependency, ensuring compliance.
Graphite Protections for secure merging
GitHub advisories integrate seamlessly with Graphite Protections to provide granular security control over pull request (PR) merging:
- Selective enforcement: Set rules to restrict merging security-sensitive files to specific teams.
- Dynamic overrides: Allow urgent merges with conditional approvals, such as overriding rules for on-call engineers.
- Automated CI checks: Ensure security-related CI pipelines are passed for PRs affecting critical paths.
For example, Graphite Protections can enforce policies like:
- "Require two approvals for changes to
config/secrets.yaml." - "Restrict merges of
security/to security team members."
improving security posture with GitHub advisories
GitHub security advisories are a powerful tool to enhance your software’s security posture. By combining these advisories with the advanced features of Graphite Protections, you can streamline vulnerability management, reduce risks, and ensure secure deployments.