Code security is paramount, and automated vulnerability detection within GitHub not only streamlines your workflow but also enhances the security of your codebase. This guide explains how to leverage GitHub's security features and Graphite Automations to effectively automate vulnerability detection.
Setting up GitHub vulnerability alerts
GitHub vulnerability detection involves setting up GitHub to automatically scan your repositories for known vulnerabilities in dependencies. Here's how to activate and manage these alerts:
- Enable dependency graph: Navigate to your repository's settings, find the "Security and analysis" section, and ensure the Dependency Graph is enabled.
- Activate security alerts: Still in the "Security and analysis" section, toggle on "Dependabot alerts" and "Dependabot security updates" to receive alerts and automatic pull requests to update vulnerable dependencies.
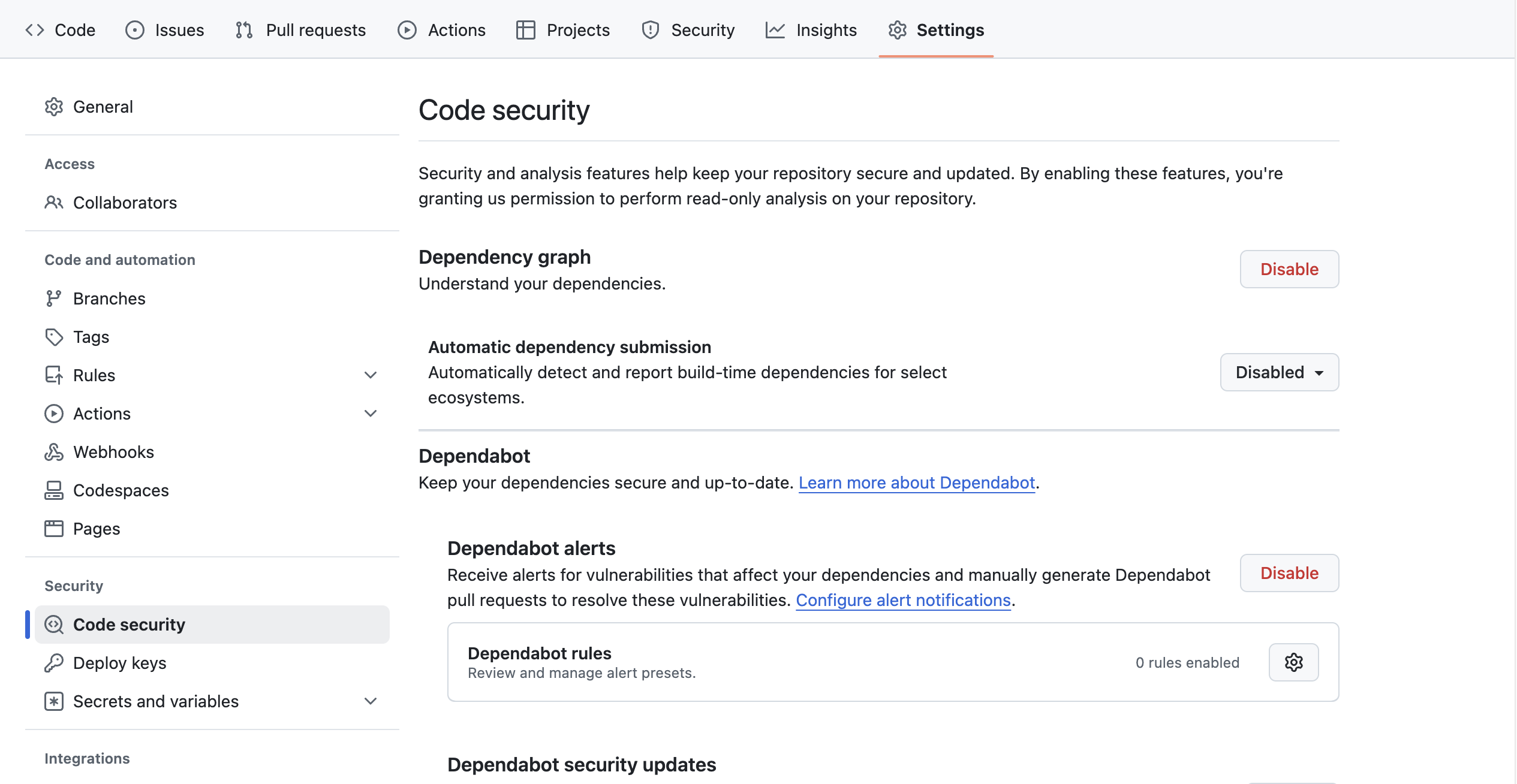
Configure Dependabot for automatic updates
Dependabot plays a key role in security automation on GitHub. It not only alerts you about found vulnerabilities but also creates pull requests to update those dependencies. Configure it by adding a .github/dependabot.yml file to your repository:
version: 2updates:- package-ecosystem: 'npm' # or another package manager like "maven", "pip"directory: '/' # Location of package manifestsschedule:interval: 'daily' # Frequency of update checksopen-pull-requests-limit: 10
This configuration checks for dependency updates daily and limits the number of open pull requests to ten.
Automating vulnerability scans with GitHub Actions
To further automate vulnerability detection, use GitHub Actions to run scans on push, pull request, or on a schedule. Here's a simple GitHub Action setup to scan for vulnerabilities using a popular tool:
name: Vulnerability Scanon: [push, pull_request]jobs:security:runs-on: ubuntu-lateststeps:- uses: actions/checkout@v2- name: Set up Pythonuses: actions/setup-python@v2- name: Install dependenciesrun: pip install safety- name: Scan for vulnerabilitiesrun: safety check
Leveraging Graphite automations for enhanced security
Graphite Automations can enhance your security by automatically responding to GitHub events based on specific triggers. For example, you can set up an automation rule in Graphite to perform actions like adding labels, notifying via Slack, or even merging pull requests when changes meet certain security criteria.
Example of setting up an automation rule in Graphite
- Create a rule: Navigate to Automations in the Graphite web app and click "Create rule".
- Specify the repository and configure the conditions you want to match, like PRs affecting sensitive files.
- Configure actions: Choose to add reviewers, set labels like "security check", or leave a comment like "Requires additional security review".
Trigger: PR contains changes to `/security/`Action: Post a comment reminding of a necessary security review
This setup ensures that any pull requests touching sensitive directories trigger a security review reminder automatically.
Summary
Automating vulnerability detection in GitHub using both GitHub's native features and external tools like Graphite can drastically reduce the risk of shipping vulnerable code. By setting up detailed alerts, automatic updates, and custom automation rules, you create a robust security posture that scales with your development efforts.