Managing secrets in GitHub Actions securely is important for protecting access tokens, environment variables, and other confidential data your workflows may use. This guide covers best practices for GitHub Action secrets management, demonstrating how to securely handle secrets to prevent unauthorized access and breaches.
Understanding secrets
Secrets are encrypted environment variables that you can use in your workflows. Unlike regular environment variables, secrets are not logged in plain text in GitHub logs and must be explicitly referenced using the ${{ secrets.NAME }} syntax.
Store secrets securely
Secure GitHub Action secrets storage is fundamental. Here’s how to properly store secrets:
Environment-specific secrets: Store secrets at the environment level rather than the repository level when possible. This limits access to the secrets based on deployment stages (e.g., production, staging).
Encrypted secrets: Use GitHub's built-in features to encrypt secrets. When a secret is saved, GitHub encrypts it and restricts access to it, ensuring that only GitHub Actions can decrypt it during execution.
Manage secrets effectively
Here are some secret management best practices**:
Minimal permissions: Apply the principle of least privilege by providing only the necessary permissions that the workflows need to function.
Audit access: Regularly review who has access to the repositories and the environments where secrets are used. Use GitHub’s audit logs to track changes to secrets.
Rotate secrets regularly: Change secrets periodically and whenever you suspect they may have been compromised.
Automate with Graphite Automations
Graphite Automations can help with secret management by automating repetitive tasks associated with secret management. For example, you can set up a rule to notify a Slack channel whenever a secret is updated, ensuring that the team is aware of changes and can verify them.
Use third-party secret managers
You can also consider using a third-party secret management service like Vault by HashiCorp, AWS Secrets Manager, or Azure Key Vault. These tools offer more robust features like automatic secret rotation, detailed access policies, and audit trails.
Creating a secret
Creating a secret in GitHub Actions involves storing sensitive data like API keys, passwords, or configuration settings securely within your GitHub repository settings. This data can then be accessed in your workflows without exposing it in your codebase. Here’s a step-by-step guide on how to create a secret in GitHub Actions:
1. Navigate to your GitHub repository
Open your browser, log into your GitHub account, and navigate to the repository where you want to add the secret.
2. Access the repository settings
On your repository page, find the "Settings" tab near the top of the page. Click on it to open the repository settings.
3. Go to the ‘Secrets’ section
In the settings menu on the left, you will find a section titled "Secrets." Click on this to access the secrets management area. Here, you will see the different types of secrets: Actions, Codespaces, and Dependabot
4. Choose the type of secret to create
Click on "Actions" to create a repository secret or variable.
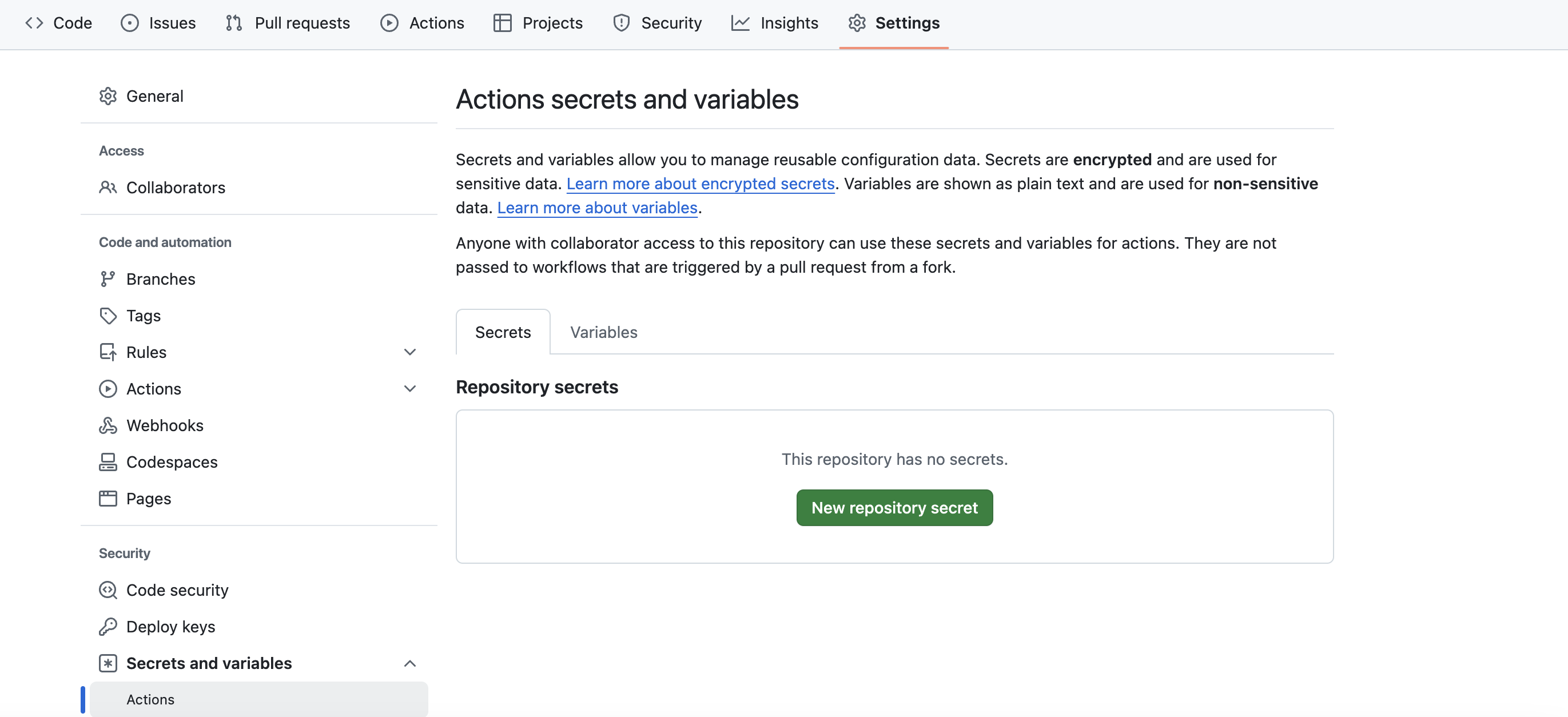
5. Create the secret
- Name your secret: Enter a name for your secret. This name will be used in your GitHub Actions workflow file to reference the secret (e.g.,
API_KEY). Make sure to use a name that can be easily recognized in your workflows. - The following rules apply to secret names:
- Names can only contain alphanumeric characters ([a-z], [A-Z], [0-9]) or underscores (_). Spaces are not allowed.'
- Names must not start with the GITHUB_ prefix.
- Names must not start with a number.
- Names are case insensitive.
- Names must be unique at the level they are created at.
- Enter the secret value: Paste the secret’s value into the text field. This is the sensitive data that you want to store securely, such as an API key or password.
- Save the secret: Click the "Add secret" button to save your secret. It is now encrypted and stored securely by GitHub.
6. Use the secret in your GitHub Actions workflow
To use the secret in a GitHub Actions workflow, reference it by using the ${{ secrets.NAME }} syntax, where NAME is the name you gave your secret. Here’s an example of using a secret in a workflow step:
name: Deploy Applicationon: pushjobs:deploy:runs-on: ubuntu-lateststeps:- name: Checkout codeuses: actions/checkout@v2- name: Deploy to serverrun: deploy_script.shenv:SERVER_API_KEY: ${{ secrets.API_KEY }}
In this workflow, API_KEY is used to set the SERVER_API_KEY environment variable which is then utilized by the deployment script.
By following these steps, you can securely manage and use secrets in your GitHub Actions workflows, keeping sensitive data safe and your automation processes efficient.
Summary
Implementing these best practices ensures your GitHub Actions workflows are secure and your secrets are well-managed. With the strategic use of Graphite Automations and third-party tools, you can streamline your secret management process, making it both secure and efficient.