A secure code review process not only identifies vulnerabilities early in the development cycle but also promotes a culture of security awareness among developers. This guide will explore the key components of code review security standards, including frameworks, exercises, and challenges. We will also discuss the role of tools like Graphite Protections in enhancing code review security.
Importance of secure code reviews
Secure code reviews are important for several reasons:
- Early detection of vulnerabilities: Identifying security flaws during the development phase is more cost-effective than addressing them post-deployment.
- Enhancing code quality: Regular code reviews promote best practices and maintain a high standard of code quality.
- Compliance with industry standards: Many organizations must adhere to specific security certifications, making secure code reviews essential for compliance.
Secure code review framework
A secure code review framework outlines the processes and methodologies used to conduct code reviews with a focus on security. A commonly adopted framework is the OWASP Secure Code Review Framework, which provides guidelines for evaluating code against various security vulnerabilities.
Key components
- Static analysis: Tools analyze the source code for known vulnerabilities without executing the program.
- Dynamic analysis: Testing is performed on a running application to identify security weaknesses.
- Manual review: Developers review code for security issues based on their experience and established best practices.
Example
Using the OWASP framework, a team might assess code against the following vulnerabilities:
- Injection flaws: SQL injection or command injection vulnerabilities.
- Authentication issues: Weak password storage or insecure session management.
- Sensitive data exposure: Insufficient protection of sensitive data in transit or at rest.
Source code review framework
A source code review framework specifically targets the analysis of source code to identify security vulnerabilities. This framework emphasizes best practices for secure coding and outlines steps for integrating security into the development process.
Secure code review exercises
Engaging developers in practical exercises is an effective way to reinforce secure coding practices. Some exercises include:
- Reviewing open-source projects: Analyze the codebase of popular open-source projects for security vulnerabilities and propose fixes.
- Participating in capture-the-flag (CTF) challenges: These competitions often include code review challenges that require participants to find vulnerabilities in provided code snippets.
Security code review examples
Providing real-world examples of security vulnerabilities discovered during code reviews can help developers understand the impact of poor coding practices. For instance:
- Example 1: SQL injection vulnerability
# Vulnerable code snippetdef get_user_data(user_id):query = f"SELECT * FROM users WHERE id = {user_id}"return execute_query(query)
In this example, the code directly interpolates the user input into the SQL query, making it susceptible to SQL injection. A secure version would use parameterized queries:
# Secure code snippetdef get_user_data(user_id):query = "SELECT * FROM users WHERE id = %s"return execute_query(query, (user_id,))
- Example 2: Insecure password storage
# Vulnerable code snippetdef store_password(password):with open('passwords.txt', 'a') as f:f.write(password)
In this case, the password is stored in plain text. A secure approach would involve hashing the password before storage:
# Secure code snippetimport bcryptdef store_password(password):hashed = bcrypt.hashpw(password.encode('utf-8'), bcrypt.gensalt())with open('passwords.txt', 'a') as f:f.write(hashed.decode('utf-8'))
Secure code review challenges
While implementing secure code reviews, teams may face various challenges, including:
- Resistance to change: Developers may be hesitant to adopt new practices or tools.
- Lack of training: Insufficient knowledge of secure coding practices can hinder effective code reviews.
- Time constraints: Tight deadlines may lead to shortcuts in the review process.
Addressing these challenges
To overcome the challenges associated with secure code reviews, teams can adopt several strategies:
Foster a culture of security: One of the most effective ways to combat resistance to change is by creating a security-first mindset within the organization. Encourage developers to view security as an integral part of the development process, not an added burden. Leaders can champion this culture by emphasizing the long-term benefits of secure code reviews, such as reduced technical debt and fewer security incidents.
Provide accessible training and resources: Address the lack of training by investing in continuous learning opportunities for the team. Regular workshops, online training programs, and peer mentoring can equip developers with the knowledge needed to conduct effective secure code reviews. Furthermore, offering certifications like the CSSLP can motivate team members to enhance their skills in secure coding and review practices.
Leverage automation to save time: To mitigate time constraints, automate parts of the security review process using tools like static analysis or code linting, which can identify common vulnerabilities before manual reviews. This allows human reviewers to focus on more complex security issues, speeding up the process while maintaining quality. Additionally, consider adopting a “shift-left” approach, integrating security checks early in the development cycle to prevent issues from piling up at later stages.
By implementing these strategies, teams can navigate the common challenges of secure code reviews more effectively, ensuring both efficiency and high-quality security standards.
Secure code review assessment
To evaluate the effectiveness of a secure code review process, organizations can implement assessments that measure adherence to security standards and identify areas for improvement. Common methods include:
- Internal audits: Regularly reviewing the code review process and outcomes to ensure compliance with established standards.
- Metrics analysis: Tracking metrics such as the number of vulnerabilities identified during reviews and the time taken to resolve them.
Role of Graphite Protections in secure code reviews
Tools like Graphite Protections can significantly enhance code review security by enforcing coding standards. Here’s how Graphite Protections can help:
Granular security control: Enforce specific security policies for PR mergeability based on sensitive file paths, security-related code changes, or specific programming languages. This ensures that only approved teams, like security, can merge high-risk code changes, such as configuration files or database schemas.
Targeted enforcement for security teams: Instead of broad, blanket policies, Graphite Protections allows security teams to define and apply merge requirements at the individual PR level, ensuring critical security-related changes are thoroughly reviewed while reducing unnecessary bottlenecks for lower-risk areas of the codebase.
Security-specific approvals: Create tailored approval workflows for security-related changes. For example, you can require that only the security team can approve changes to sensitive areas like authentication code or infrastructure configurations, ensuring no unreviewed or unapproved changes bypass security standards.
Automated CI security checks: Ensure that PRs affecting sensitive parts of the codebase pass specific security-related CI checks, such as static code analysis or vulnerability scans. This reduces the risk of security vulnerabilities being introduced by automatically enforcing code quality gates before the PR can be merged.
Security overrides for emergency situations: In cases of urgent security fixes, Graphite Protections allows you to configure override options—such as permitting emergency changes even if not all standard requirements are met. This ensures critical patches can be deployed quickly without compromising overall security governance.
GitHub integration: Graphite Protections integrates with GitHub’s Branch Protection Rules, enabling security teams to incrementally migrate their merge requirements and securely manage their workflow without disrupting existing protections. Both systems work together to enforce the highest security standards.
Clear mergeability UI for security teams: The PR page in both Graphite and GitHub shows security reviewers exactly what steps remain before a PR is secure and mergeable. This transparency helps teams ensure that all security requirements are met and reduces the risk of human error.
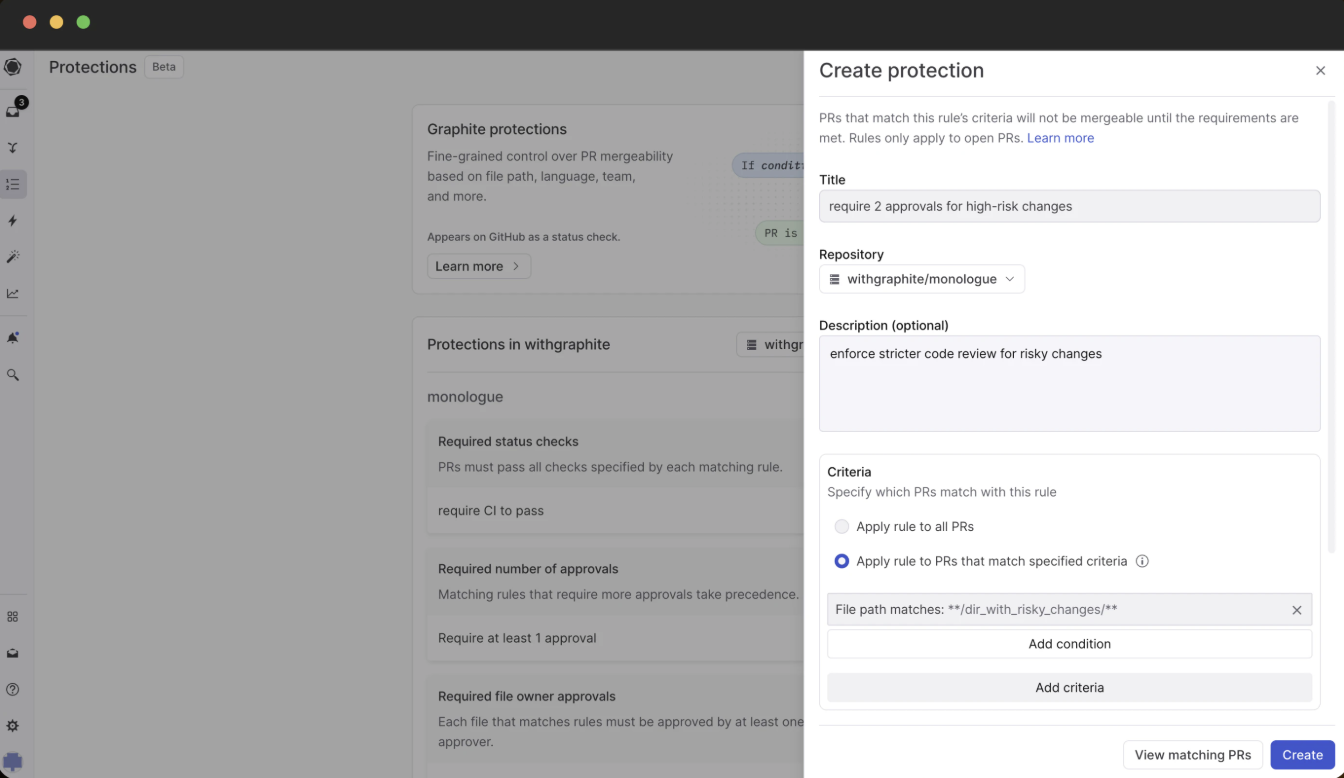
By leveraging Graphite Protections, security teams can create a robust, secure code review process that is comprehensive, flexible, and tailored to the unique security needs of each code change.
Key takeaways
Implementing robust code review security standards is essential for safeguarding software against vulnerabilities. By adopting secure code review frameworks, engaging in practical exercises, and leveraging tools like Graphite Protections, organizations can significantly improve their code security posture. Regular assessments and continuous training further ensure that teams stay up-to-date with evolving security practices and challenges.